Synthetic telepathy “Artificial Telepathy”
Synthetic telepathy“Artificial Telepathy” is the art of electronically transfering thought directly to and from a brain. The primary objectives of www.mindcomputers.com are to expose technology that can provide point to point communication from one brain to another, to localize unwanted sources of telepathic communication, and to provide evidence that technologically implemented telepathy is possible.
Technology to block unwanted voices is being investigated. A key objective is to prove the existence of criminals who abuse existing synthetic telepathy technology. Further objectives include investigating other computational substrates than brain tissue. www.mindcomputers.com is also interested in marketing existing synthetic telepathy technology. For justice and medical purposes only.
Welcome to Mind Computers
The experience of synthetic telepathy or“Artificial Telepathy” is really not that extraordinary. It’s as simple as receiving a cell-phone call in one’s head.
Indeed, most of the technology involved is exactly identical to that of cell-phone technology. Satellites link the sender and the receiver. A computer “multiplexer” routes the voice signal of the sender through microwave towers to a very specifically defined location or cell. The “receiver” is located and tracked with pinpoint accuracy, to within a few feet of actual location. But the receiver is not a cell phone. It’s a human brain.

Out of nowhere, a voice suddenly blooms in the mind of the target. The human skull has no “firewall” and therefore cannot shut the voice out. The receiver can hear the sender’s verbal thoughts. The sender, in turn, can hear all of the target’s thoughts, exactly as if the target’s verbal thoughts had been spoken or broadcast. For this reason, the experience could be called “hearing voices” but is more properly described as “artificial telepathy”.
Now, if artificial telepathy were entirely voluntary, like a conversation between friends sitting across the room from one other, it might be kind of cool. One could talk back and forth with one’s friend, exchanging verbal thoughts exactly as if speaking on the phone, but without ever using one’s voice or mouth. It’s a completely silent, subvocal form of speech. Between lovers, this would be beautiful.
The problem is that artificial telepathy provides the perfect weapon for mental torture and information theft. It provides an extremely powerful means for exploiting, harassing, controlling, and raping the mind of any person on earth. It opens the window to quasi-demonic possession of another person’s soul.

When used as a “nonlethal” weapons system it becomes an ideal means for neutralizing or discrediting a political opponent. Peace protestors, inconvenient journalists and the leaders of vocal opposition groups can be stunned into silence with this weapon.
Artificial telepathy also offers an ideal means for complete invasion of privacy. If all thoughts can be read, then Passwords, PIN numbers, and personal secrets simply cannot be protected. One cannot be alone in the bathroom or shower. Embarrassing private moments cannot be hidden: they are subject to all manner of hurtful comments and remarks. Evidence can be collected for blackmail with tremendous ease: all the wrongs or moral lapses of one’s past are up for review.
Like a perverted phone caller, a hostile person with this technology in hand can call at any time of day, all day long. Sleep can be disrupted. Prayers can be desecrated, religious beliefs mocked. Business meetings can be interrupted, thoughts derailed. Love can be polluted, perverted, twisted, abused. Dreams can be invaded, fond memories trashed.
The attacker cannot be seen or identified, the attack cannot be stopped, and the psychological damage is enormous. But there is no physical damage, not one single mark is left on the body and there is absolutely no proof that any crime or any violation ever took place! Everything that “happens” to the victim happens inside the victim’s head. What physical evidence is there to give the police? Without physical evidence, how can one photograph the “crime scene” or fingerprint the stalker? There are no footprints leading to or from the scene. Indeed, there is no physical scene at all, and no evidence that an attack ever took place.
Most people who experience this abusive form of “artificial telepathy” feel as if their mind has been raped. They find themselves hunted, stalked, harassed and abused by a person or persons who refuse to give their names, who defile one’s mind with the most foul and perverse language imaginable, and who refuse to hang up or go away. The caller or callers delight in the perverse and sadistic torture of their targets. Furthermore, they delight in violating the privacy of their targets, reading the target’s mind and commenting on everything the target thinks, in an effort to demonstrate as brutally as possible that the target has no privacy at all.
Imagine what a man might do if he found a ”cell phone” that allowed him to dial into the heads and the private thoughts of anyone on earth. The temptation to choose a target at random and start spying on or abusing that person would be enormous, almost irresistable. It could become a sick and twisted hobby, a guilty pleasure very quickly. Put into the hands of a secret police unit, the potential for abusing such technology is even more chilling.

Synthetic Telepathy system, would be intelligence gathering and interrogation. As a communication system, it would have a limited appeal as any nation with a similar setup could either listen in, or pretend to be the A.I. interface. As such, it raises important ethical and legal questions, especially the question of secrecy given that all major governments would be aware of the system. Given that no law permits this type of interrogation, its secrecy may be more to do with criminal activity on behalf of the security agencies, rather than national security.
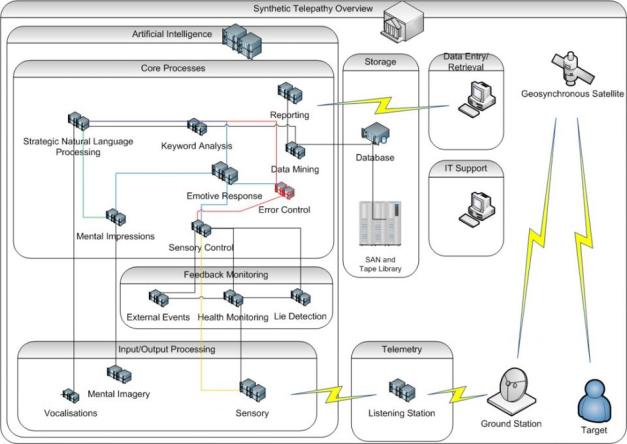
Its All About The Transceiver!
To understand how this works, it is best to start with the target, then trace backwards and identify each of the required subsystems. If we look at the last diagram to the left, we can see that the key to this system is its ability to both listen and respond to the electrical activity of the brain implant from satellite.

Now, the natural reaction of a normal and intelligent person who undergoes the horrible experience of mind rape for the first time is to panic and reach for a real phone. They call family, contact their doctor or call police with a bizarre complaint that “someone is beaming voices into my head.”
But if the police are the ones behind the abuse, the victims aren’t going to get much help, are they? And if the police are not the perpetrators, then how are they to make an arrest? It’s much more convenient and easy to believe that the caller is a nutcase.
In short order, the victim of mind rape finds herself or himself undergoing the additional humiliation of being carted off to the psych ward, often being committed involuntarily by a loved one “for one’s own good.”
The more vehement the efforts to prove that the voice or voices in one’s head are “real”, the more smug become the smiles of the medical doctors, who gently insist that such technology does not exist, that the voices cannot possibly be real, and that one must take a powerful, down for a good long rest.
The experience of “hearing voices” — especially voices that give a running stream of negative abuse — will gain one automatic admission to the rubber room. Indeed, hearing voices is a classic example of schizophrenia. If you hear voices, you are, by definition, crazy.
Yet when released from the psych ward with an expensive supply of meds, “voice hearers” often find that the meds are ineffective — exactly as one would expect if their problem had nothing to do with brain chemistry and everything to do with a bio-electronic attack by unseen stalkers.
Voice hearers often puzzle psychiatrists, because many of them don’t fit the classic model of schizophrenia, which usually begins onset in the early twenties. The victims of Synthetic telepathy “artificial telepathy” are often well into their thirties or fourties and many have no prior history of serious mental illness or drug abuse. Many seem to be alert, healthy, and rational even while insisting that they can hear voices. They agree with the psychiatrists that, yes, they are depressed, but who wouldn’t be a bit depressed under such trying circumstances? To be stalked and verbally bullied every waking hour of the day is a form of mental torture.
Victims of mind rape quickly learn not to discuss their “psychological problems” with family and coworkers. It’s embarrassing, it’s bizarre, it gets very little sympathy and only serves to alarm most people. The only way that another person can “help” is to suggest that the mind rape victim see a psychiatrist, who will promptly double one’s dose of psych meds and antidepressants. The result is a very stiff medical bill, which only adds financial pain to the mix. And the verbal harassment continues.
As they learn to endure their daily torture, voice hearers can usually return to mainstream life, where they are able to carry on intelligent, coherent conversations, hold down jobs, and function quite normally. In fact, if they don’t discuss their “problem” they usually can’t be told apart from normal people on the street. Because they are normal people.
The growing number of voice hearers in our society is therefore well masked. Those who continue to insist that there is a “secret society of people beaming voices into our heads” are simply laughed into silence or labelled paranoid schizophrenics. They are completely discredited. In fact, many voice hearers have internalized the idea that they are mentally ill, and they struggle to understand how their “auditory hallucinations” could continue to seem so very, very real.
Naturally, many of these voice hearers are deeply confused. They turn to support groups, including such on-line communities as the Voice Hearers’ support group at Yahoo.com.
Anyone who doubts that “artificial telepathy” exists need only contact such a Voice Hearers community, where they will encounter people who continue to insist that they are being harassed by real people using an unknown or unexplained technology.

Surprisingly, there is a tremendous amount of scientific literature and circumstantial evidence to back up that claim.
In the following posts, we will explore the history of synthetic telepathy and learn the names of the scientists who developed this sinister technology. We will also identify and examine some of the government agencies that are fielding and using this weapon of torture against innocent civilians.
By Magnus Olsson, Mindtech (Sweden)

Brain “Mind”Link Technology
The NSA – Behind The Curtain


Today we will take an in-depth examination of the NSA’s global intelligence gathering network. What you are about to read will come as an eye-opener and represents the current state of the NSA’s capabilities. Some of this will be expected, some of it will come as a shock.
What you will learn is that the technology that underpins this global listening network is a lot more advanced than governments would have you know. Usually wrapped up in basic, generalised, descriptions the general public is kept blind to the current state of technological development.
We will take this examination in three major parts. The first part will examine the core processing system. Once this part is understood, we can then look at how information flows to and from this core and where it is obtained from. Finally, we will examine how this information is used by the NSA.
I will cover as much as possible about this system, but the scope is very large. In general, any use of this data that the reader can observe is most likely already being conducted.


The scope of the NSA’s infrastructure is mind boggling to say the least. Heavily compartmentalised, the entire array of systems is shielded from the average NSA employee as much as it is shielded from the public. That said, once you understand the core of the NSA, you will be in a position to see how information flows in and out of this core.
Mr Computer
The NSA is built around a super-computer bound Artificial Intelligence known only as “Mr Computer” in the civilian world. This is not your average A.I., no basic set of responses or a mere dedicated algorithm that can spot patterns. Mr Computer is an entity or being in his own right. A sentient computer system as complex as any human.
Comparable to VMware in a way, an instance of Mr Computer can be started at a moments notice. Within seconds, a fully fledged virtual intelligence agent, ready to analyse the information that has been piped to him, can be up and running.
Mr Computer is competent enough to handle real-time interaction without human intervention. Mr Computer understands and speaks all modern languages and even a number of dead ones. Able to intelligently converse and express its own opinions, Mr Computer collates information from disparate sources and compiles them into concise reports that do not miss the smallest detail or nuance.
Mr Computer’s capabilities and human-like reasoning cannot be understated.











i beleave this can also be done with brain entrainment techniques and eeg readings with a maser beam.
I second that : and i have photos of the crime scene, EEG maps of my brain,during dis entrainment therapy. That’s how you photograph the crime scene
This is very serious. I have been victimized since at least 1999. In my case, cell phone technology is integrated and information about my victimization and my private life have been passed on to others. I went to the police and on the bus home, there were college-age people looking at their phones and making comments of my conversation inside the police station.
This is a way to circumvent the rights and privileges that we have. It can also be done from a distance without leaving an image on camera. HIPPA Laws for instance – the user can see from a distance what is transpiring during a medical exam. The technology has advanced so that the user can know what the target is seeing and hearing, so they can look at what is going on during your doctor’s appointment without having to Subpoena or request medical records
I am worried because I have “spotters” in the area where I live. The scary thing is that even emotions can be transmitted via what I call the “carrier wave.” I was lying down and suddenly I felt a guy’s love. I also sensed vulnerability. There was a woman working at our office a few years ago. She made the remark, and I am not an anxious person, she told me out of the blue to “calm down” and I felt myself becoming calmer, as if she willed me to be calm.
The CIA had MK Ultra. Electromagnetic wave technology was part of it. It was supposed to be shut down. It was n ot – it was moved under another agency – the NSA. Further food for thought – the NSA has had the capabilities and this incredible technology since at least 1999 – 2 years before Sept. 11th. I believe that Sept. 11 could have been prevented. My theory is that Sept. 11 happened to bring terrorism to the forefront of American’s minds to that the NSA would not be questioned, so that there would not be another church committee. The NSA may currently be in contempt of the U.S. Senate by using technology that was ordered by the Senate Intelligence Committee to be shut down.
There are the 4th Amendment and 4th Amendment rights that protect against searches. This technology enables people to see what is going on inside of an individual’s residence. Attorney-client privilege is also in danger, as well as this technology enables people to see how things are being done, so that even if you don’t give out a recipe, they can still see with the aid of this technology, how your food is made.
Below is an email I am sending around to various organizations without very much luck, My name is Dominic Friscia. I live in Saugus, California. I am a subject to organized stalking, human cage and mental slavery technology. I am contacting you because I am in isolation. I was curious to know if you were in contact or know anybody that you trust. I came across this page after being in contact with ICAACT, International Center Against Abuse of Covert Technologies. I have also found Dr. Robert Duncan and Mark Rich to be very insightful and helpful as literary references, particularly Mark Rich’s profile of psychopaths and his background provided on schizophrenia programs in Russia East Germany, Nazi Germany and their expansion in the United States under the elite rulers. Schizophrenia is a government torture program of covert control to destroy lives and ultimately minds. I am pointing people towards some good evidential literature on this topic by Dr. Robert Duncan. He is a Department of Defense-CIA whistle blower who is part of a group of scientists trying to spread awareness about the existence of technologies that produce ‘schizophrenia’ or that are part of schizophrenia programs run by the government. He discusses how people are inserted into these programs against their will. I provide the information so that I may appear less insane to you. He has 2 books:
1. The Matrix Deciphered and
2. Project Soul Cathcher-Secrets of Cyber and Cybernetic Warfare Revealed
You are not familiar with and do not engage in Organized Gang Stalking and Mental Slavery Torture: I can recommend these pages in The Matrix Deciphered.
– Mental Illness Taboo To…pic and preferred Coverup Technque for last few decades page 73
– Psychotronic Slavery in U.S pg 199
– Suffering and Mind Control pg 192
– Dr. Robert Duncan Genius or Insanity pg 75
– Dr. Robert Duncan Page 77 Strategic Deception Purging the Erronous
– Dr. Robert Duncan Non-Lethal Weapons Lie pg 64
– Discrediting Method “The Method”page 60 and 61
– Strategic Deception pg 58
– Methods of Discrediting pg 57
– Introduction pgs 18-20
– My Hell-pg 29
This links to it:
http://projectavalon.net/forum4/showthread.php?56002-Must-Read-The-Matrix-Deciphered-by-Dr-Robert-Duncan
I’ve gotten into limited contact with people through Christians Against Mental Slavery. I found it helpful that they put together a packet on organized stalking to explain it. I am thankful that this information is there. I am in the process of leaving the country because I cannot go anywhere or do anything without being in a cage. I plan to go to Dublin once I get citizen ship through the EU. Do you know trustworthy people in California I can meet with? I want to press charges on the people who have participated in my harassment, stalking and abuse. In my case, I am aware of reasons why I am targeted. In my case I know that Occupy is homeland security. They responded by turning my home into a prison, put me under brain monitoring and DE, following me and my father around like undermench, placing me in a cage, in which people take amusement at harassing, abusing and systematically depressing me and subjecting me to remote influencing technologies and psychotronics.
This is a blog I am utilizing. I attempted to start this blog and subsequently became aware that Occupy was homeland security. http://fredrickfredricks.blogspot.com/: And this is another blog I am utilizing: http://69centsforhaitioccupyisafascistfront.wordpress.com/ Any information or help is appreciated.
Sincerely,
Dominic Friscia
dominicfriscia@yahoo.com
415-271-7452
Im going through the exact same thing people are using it how can I use it because I actually know the people that’s in my head doing it. It very damaging in my life as we speak, (561)202-7128
Hi, I have experienced the same symptoms of electronic mind control/mind torture. I work at a bank in Johannesburg, South Africa. Cops have pretended I am under surveillance/under arrest and illegally psychologically torture me and my family for almost 2 years viciously at workplace and residence. Experienced brain zaps, blows to skull, audible voices, nerve tingling/twitches, holding of blood on forehead (attempted blood clotting), physical burn on back of calf, etc. This started after altercation with former neighbours (who may be cops) at Fourways residence, who stalked me from one residence to another and spread false rumours at workplaces, facebook, etc. This is a gross violation of human rights abuse MIND RAPE.
Quantum Consciousness:
“The quantum mind or quantum consciousness hypothesis proposes that classical mechanics cannot explain consciousness, while quantum mechanical phenomena, such as quantum entanglement and superposition, may play an important part in the brain’s function, and could form the basis of an explanation of consciousness.”
Source: http://en.wikipedia.org/wiki/Quantum_mind
Brian David Josephson & Josephson Effect:
Brian David Josephson, (born 4 January 1940) is a Welsh physicist. He became a Nobel Prize laureate in 1973 for the prediction of the eponymous Josephson effect.
As of late 2007, he was a retired professor at the University of Cambridge, where he is the head of the Mind–Matter Unification Project in the Theory of Condensed Matter (TCM) research group. He is also a fellow of Trinity College, Cambridge.
Josephson is best known for his pioneering theoretical work on superconductivity, earning him a 1/2 share of the 1973 Nobel Prize for Physics. Specifically, it was awarded for “his theoretical predictions of the properties of a supercurrent through a tunnel barrier, in particular those phenomena which are generally known as the Josephson effects”, which led to the invention of the Josephson junction. These junctions are key components in devices used to make highly sensitive measurements in magnetic fields. Further use for his discoveries was realized by researchers at IBM who, by 1980, had assembled an experimental computer switch structure, which would permit switching speeds from 10 to 100 times faster than those possible with conventional silicon-based chips, vastly increasing data processing capabilities.
In 2001 Josephson’s views on the paranormal were under the spotlight when he wrote about them in a booklet to accompany six special stamps to honor the 100th anniversary of the Nobel prize. The Royal Mail had sent Josephson a request to write a small article about their award and the implication of research in their field they could use in conjunction with the special Nobel Centenary stamp issue. He wrote the following:
“Physicists attempt to reduce the complexity of nature to a single unifying theory, of which the most successful and universal, the quantum theory, has been associated with several Nobel prizes, for example those to Dirac and Heisenberg. Max Planck’s original attempts a hundred years ago to explain the precise amount of energy radiated by hot bodies began a process of capturing in mathematical form a mysterious, elusive world containing ‘spooky interactions at a distance’, real enough however to lead to inventions such as the laser and transistor. Quantum theory is now being fruitfully combined with theories of information and computation. These developments may lead to an explanation of processes still not understood within conventional science such as telepathy, an area where Britain is at the forefront of research.”
In 2005, Josephson said that “parapsychology should now have become a conventional field of research, and yet parapsychology’s claims are still not generally accepted”. He compared this situation to that of Alfred Wegener’s hypothesis of continental drift, where he believed there was initially great resistance to acceptance despite the strength of the evidence. Only after Wegener’s death did further evidence lead to a gradual change of opinion and ultimate acceptance of his ideas. Josephson said that many scientists are not yet swayed by the evidence for parapsychology and the paranormal. Josephson contends that some scientists feel uncomfortable about ideas such as telepathy and that their emotions sometimes get in the way.
Source: http://en.wikipedia.org/wiki/Brian_David_Josephson
Quantum tunneling falls under the domain of quantum mechanics: the study of what happens at the quantum scale. This process cannot be directly perceived, but much of its understanding is shaped by the macroscopic world, which classical mechanics can not adequately explain. To understand the phenomenon, particles attempting to travel between potential barriers can be compared to a ball trying to roll over a hill; quantum mechanics and classical mechanics differ in their treatment of this scenario. Classical mechanics predicts that particles that do not have enough energy to classically surmount a barrier will not be able to reach the other side. Thus, a ball without sufficient energy to surmount the hill would roll back down. Or, lacking the energy to penetrate a wall, it would bounce back (reflection) or in the extreme case, bury itself inside the wall (absorption). In quantum mechanics, these particles can, with a very small probability, tunnel to the other side, thus crossing the barrier. Here, the ball could, in a sense, borrow energy from its surroundings to tunnel through the wall or roll over the hill, paying it back by making the reflected electrons more energetic than they otherwise would have been.
Source: http://en.wikipedia.org/wiki/Quantum_tunnelling
http://upload.wikimedia.org/wikipedia/commons/f/f5/Photoelectric_effect.svg – The photoelectric effect. Incoming photons on the left strike a metal plate (bottom), and eject electrons, depicted as flying off to the right.
The Quantum Machine:
The first quantum machine was created on August 4, 2009 by Aaron D. O’Connell while pursuing his Ph.D. under the direction of Andrew N. Cleland and John M. Martinis at the University of California, Santa Barbara. O’Connell and his colleagues coupled together a mechanical resonator, similar to a tiny springboard, and a qubit, a device that can be in a superposition of two quantum states at the same time. They were able to make the resonator vibrate a small amount and a large amount simultaneously—an effect which would be impossible in classical physics. The mechanical resonator was just large enough to see with the naked eye—about as long as the width of a human hair. The groundbreaking work was subsequently published in the journal Nature in March 2010. The journal Science declared the creation of the first quantum machine to be the “Breakthrough of the Year” of 2010.
In order to demonstrate the quantum mechanical behavior, the team first needed to cool the mechanical resonator until it was in its quantum ground state (the state with the lowest possible energy). Specifically, a temperature T « hf/k was required, where h is the Planck Constant, f is the frequency of the resonator and k is the Boltzmann constant. Previous teams of researchers had struggled with this stage, as a 1 MHz resonator, for example, would need to be cooled to the extremely low temperature of 50 μK. O’Connell’s team constructed a different type of resonator, a film bulk acoustic resonator, with a much higher resonant frequency (6 GHz) which would hence reach its ground state at a (relatively) higher temperature (~0.1 K): this temperature could then be easily reached with a dilution refrigerator. In the experiment, the resonator was cooled to 25 mK.
h = ℏ (an atomic system at absolute zero retains an energy of ½hν)
T« ℏf/k = (Planck’s constant / (2 * pi)) * ((3.28 GHz) / Boltzmann constant) = 25 mK (millikelvin)
The film bulk acoustic resonator was made of piezoelectric material, so that as it oscillated its changing shape created a changing electric signal, and conversely an electric signal could affect its oscillations. This property enabled the resonator to be coupled with a superconducting phase qubit, a device used in quantum computing whose quantum state can be accurately controlled.
In quantum mechanics, vibrations are made up of elementary vibrations called phonons. Cooling the resonator to its ground state can be seen as equivalent to removing all of the phonons. The team was then able to transfer individual phonons from the qubit to the resonator. The team was also able to transfer a superposition state, where the qubit was in a superposition of two states at the same time, onto the mechanical resonator. This means the resonator “literally vibrated a little and a lot at the same time”, according to the American Association for the Advancement of Science. The vibrations lasted just a few nanoseconds before being broken down by disruptive outside influences. In the Nature paper, the team concluded “This demonstration provides strong evidence that quantum mechanics applies to a mechanical object large enough to be seen with the naked eye.”
Source: http://en.wikipedia.org/wiki/Quantum_machine
Frequency of Quantum Consciousness (maybe):
T« ℏf/k = (Planck’s constant / (2 * pi)) * ((40.66 THz) / Boltzmann constant) = 99.3569983 degrees Fahrenheit (brain temp is higher than core body temp by 0.39 to 2.5 degrees Celsius)
So this means that you would need to have a frequency of higher than 40.5 THz in order to perform quantum tunneling needed to produce telepathy for the human brain, seeing as your body (97.3-99.1 °F) and brain (36.69-39.8 °C) operate at specific temps during times of good health.
Optical Rectification:
In optical rectification, a high-intensity ultrashort laser pulse passes through a transparent crystal material that emits a terahertz pulse without any applied voltages. It is a nonlinear-optical process, where an appropriate crystal material is quickly electrically polarized at high optical intensities. This changing electrical polarization emits terahertz radiation.
Because of the high laser intensities that are necessary, this technique is mostly used with amplified Ti:sapphire lasers. Typical crystal materials are zinc telluride, gallium phosphide, and gallium selenide.
The bandwidth of pulses generated by optical rectification is limited by the laser pulse duration, terahertz absorption in the crystal material, the thickness of the crystal, and a mismatch between the propagation speed of the laser pulse and the terahertz pulse inside the crystal. Typically, a thicker crystal will generate higher intensities, but lower THz frequencies. With this technique, it is possible to boost the generated frequencies to 40 THz (7.5 µm) or higher, although 2 THz (150 µm) is more commonly used since it requires less complex optical setups.
Source: http://en.wikipedia.org/wiki/Terahertz_time-domain_spectroscopy
Wireless data transmission using THz radiation:
In May 2012, a team of researchers from the Tokyo Institute of Technology published in Electronics Letters that it had set a new record for wireless data transmission by using T-rays and proposed they be used as bandwidth for data transmission in the future. The team’s proof of concept device used a resonant tunneling diode (RTD) in which the voltage decreased as the current increased, causing the diode to “resonate” and produce waves in the terahertz band. With this RTD, the researchers sent a signal at 542 GHz, resulting in a data transfer rate of 3 Gigabits per second. The demonstration was twenty times faster than the current Wi-Fi standard and doubled the record for data transmission set the previous November. The study suggested that Wi-Fi using the system would be limited to approximately 10 metres (33 ft), but could allow data transmission at up to 100 Gbit/s.
Source: http://en.wikipedia.org/wiki/Terahertz_radiation
Terahertz radiation can potentially be blocked with radiation shielding like http://www.rockyflatsgear.com/large-radiation-shieled-sheet-green-black.html
Telepathy (synthetic or natural) is 100 percent real. The quantum machine is a reality and establishes without a question that for quantum systems which are invariant under time reversal the Hamiltonian can be made real and symmetric, so that the action of time-reversal on the wave-function is just complex conjugation. If such a Hamiltonian has a unique lowest energy state with a positive real wave-function, as it often does for physical reasons, it is connected to a stochastic system in imaginary time. This relationship between stochastic systems and quantum systems sheds much light on supersymmetry. Imaginary time = absolute time = Eye of Providence
I love your article. It is very well written and informative. Please consider this a challenge Question?
SInce the day I was born, I have been observed by satellite. I never knew whether a brand new car or yacht would fall out of the sky when I think of the excitement others would create for their religious and community promises. Recently I discovered that someone else, a government perhaps, has the ability to not only ‘link an individual’ to another using a device such as a satellite but also the technology to cause harm to either brain unlike loud music or “phasers”. Consequentially teleportation effects the relationship of a concious and it’s memory then simutaneously… either origin or ability to pay! Who are the people who have been using the devices? Doctors, Physicians, Someone who needs to be shot in the head in public. I have had this issue with them for more than 10 years and want to know exactly where they are and why the United States thinks the technology is worth concealing someone chosen to defend himself.
This technology and the criminals who perpetrate it are constantly in violation of our law against illegal telephone taps! Any person who knowingly receives both sides of another persons phone call (including cellular) is guilty of a class b felony punishable by 5-20 years in prison per incident!
have had my thoughts raped and stolen for 9 months now. affects so far include theft of identity, theft of ideas, and theft of large sums of cash destined for my accomplishments. is there an actual law on the books regarding theft by telepathy. looking forward to your reply
Check out Michigan’s anti-electronic harassment law. Amway was messing with their cult and their HQ is in Michigan. Google ‘amway michigan electronic harassment,”
Heya i’m for the first time here. I came across this board
and I to find It really helpful & it helped me out a lot.
I hope to give something again and help others like you aided me.
What can we do against brain control?
1. Build a mini tesla plasma shield to protect our brains (see youtube video how to make one) against the brain control of the Satanists that want to kill most of us with synthetic telepathy and directed energy weapons.
2. Find a way to make the (illegal) voice to skull messages audible. See Neurophone silent sound patent and Synthetic Telepathy (Malech Patent). The voices possibly everybody hears intra cranially are from a quantum computer that is able to speak any language, send ideas in peoples own inner voice and control emotions. The shield and instrument to make the voice to skull messages audible should both be available to the public. Make some money. What do you say?
3. Switch off or sabotage the brain control equipment, Beast Computers and switch of the HAARP generator.
4. Educate people about the brain control going on at the moment and teach them what they can do to survive and control themselves: opposite next idea, recovery begins with non compliance, trust no one nothing is what it seem stay pro active rather than reactive united we stand. Expose their strategy: divide to defeat and problem reaction solution. Sometimes it is kill or be killed. Ideas are bullet proof C D roms are E M P proof. Build in ground resistors against the upcoming solar storm predicted by NASA which can be generated with HAARP according to the Doctor Eastlund HAARP patent.
5. Use hypnotic triggers used in their brain control to shut down their internal computers like disarm disarm disarm the Alpha and Omega pedo Jesuit military order. Use their own technology weapons and torture devices against them until they are exterminated in stead of the 93% of the worlds population they want to eliminate in their third world war for their Satanic New World Order endorsed by the Vatican. Cosmic entity. Me. You and me together baby.
6. O la D yay o la d yo. Do a hypnosis. Hypnotize everyone so the perpetrators loose control and power to the peaceful. Program them to make everyone eternal and create a non fictional Utopian perfect society in which we all will live eternally. Enforce basic human rights with the new technology (robots, synthetic telepathy, scalar technology, quantum computers) rather than depopulate in violation of the Genocide Convention. Do not exterminate your self and others by helping the perpetrators to destroy the people that expose them. Some things like controlling muscle movement can not be controlled with a hypnosis but we can program ourselves to compare every idea to the opposite next idea to come up with the best ideas to save our selves, make ourselves eternal and bestow maximum fulfilment upon us all.
I enjoyed your response. Did you forget,”bomb the telemetry dishes”? or lynch the surgeons who implant patients for research without consent?
Im 16, i have been hearing voices for the past year everyday non stop. They have been reading my thoughts and memories and critisizing my every movement. I tried ignoring it but it just got worst , as they talk i start to feel thier words through mythroat as if i was bieng forced to say something , and then i started getting muscle twitches and massive headaches like as if my brain was being twisted, one time i was in class and i felt like i was gonna have a siezure i coupdnt touch anything without feeling this cold irritating sensation through my legs and fingernails etc i can barley think without getting this hard pressure in my head. The voices have caused me to move away from my mom “who i told and refused to believe me” with my dad and thats when things got worse.. I know whos voices they are and ive confronted the “PEOPLE ” but they just blew me off and denied acusations or just plaid dumb, i didnt know then but now i know that me going mad was actually provoked. They play mind games with me telling me things like im being ivestigated or im a nucleur warhead , or that theyve fused my mind with thiers and then, they try to sweet talk me like they are trying to hypnotize saying that they arent who the are , the voices arent theirs and that they are helping me.They also non stop taunt me saying that theyre laughing at me there not gonna let me grow or better than them,,the time i dont realy care of these things . I know i come off as “crazy but Im not . But reallythey are driving me crazy and they try and use it against me . Please I dont know wat to do..if there is any way u can help PLEASE WRITE ME BACK !!!!!!
Its an advanced AI. Its mostly if not completely automated. You cannot stop it. You must learn to ignore AND live with the voices and the reactions they cause within you. Many sounds and things you think people are saying are NOT real – they’re projected into your head. Some things are REAL as others’ around you are mind controlled. IGNORE IT/THEM. Its the best way to live your life.
Don’t see a psychiatrist – it won’t help. You are amongst the 10% of the population (not all affected yet) who are partially immune to the influence of this technology as statistical anomalies within the client population.
1. Keep everyone as close as possible, don’t isolate your self, its very hard to convince someone that something like that exist. If you start explaining, you will be considered delusional, paranoid, psychotic.
2. Keep yourself busy, talk, go places with many people, malls, parks, ignore the voices, isolation, fear and paranoia is your worst enemy, don’t let it convince you that someone is reading your memory, and if they do: who cares!
3. If you think that someone is following you, listening to you, or giving you suggestions, ignore it! most likely there is no one. There are few tricks that may trigger / induce psychosis that will make you feel like some people say “gangstalked”, ignorance is half way out.
4. They are not investigating anything, don’t be tricked into anything, officially this type of technology and people don’t exist, they can not go against you and you can not go against them. Don’t let them lure you in to trouble.
5. Be good with people, if experience headaches or anything life concerning, talk to doctor, just don’t talk for mind control too much, it may and will sound crazy…
6. Type of people and technology that can do such things can be simply described as “delusional psychopathic whores”, sooner or later they will have to come out of the closed, I hope they, and the people that finance them (government funds and private research companies) get hit as hard as they deserve, they are going against the whole humanity, even against themselves and future of their kids.
ps. dont worry about thoughts reading, 90% of the info that they can possible get, if such technology exist, will be inaccurate attempt…:).
Good luck!
This will help you:
http://mind-computer.com/gold-against-mind-control/
not sure if i can help but i know about what you say If you like stay in touch and let me know how your doing Been going through something similar for the past 9 months Stay strong and do your best to stay maintained
My name is leslie Williams Lisa PLEASE STAY SAFE and Understand I walk with you throughout everything you experience Im trying to say YOU ARE NOT ALONE you are loved and you matter and I dedictae that statement to every targeted Individual EVERYONE I am a target Victim Activist of this Crime their targeting me in San diego Like you whould not beleive in San Diego and you whouldnt belive what I know Ive been on national Radio shows and have gotton some measured exposure I do what I do for you and to expose the crimminals who do these crimes and the one’s who protect them and we all know who they really are
I know there is evidence of this being done and it’s ignored by the medical community, which has extreme influence over the legal community. I could see the medicated shell that the voices and the shocks are originating from in the X-Ray that was taken of me and I have video evidence of the shocks, the voices, the medications I was taking conducting magnetism, and medications still gathering onto the back of my bottom incisors from my saliva years after ceasing to take them. This is evidence that medicated shells have been formed over the brains of hapless victims duped by doctors into thinking the meds just get filtered through the biochemistry. There are links to this evidence on my blog at:
http://imaginesvinco.blogspot.com/
Afternoon
I require some information please on the ethical uses of RFID Chips on humans, as well as how I would go
About finding an RFID chip reader in order to read the serial number thereof if found in my body ?
I believe that I have had an RFID Chip implanted into my body against my will possibly during an operation
that I had on my left arm after a car accident in +- June/July 2007 at Linksfield hospital and or during my
breast augmentation that I had in December 2009 at Rosebank clinic. I just would like to state that I most
certainly would not have consented to such, as it goes against all my beliefs both physically and spiritually.
(Can these RFID chips ever be small enough to be inhaled into the olfactory system ?)
I feel as though my dreams are being recorded and that my mind is being read through the program
As well as my physical body being effected by these frequencies in a negative manner. I feel this way due to
Acquaintances and non as such, discussing certain variants of my life that should be private and in
No way presented for public discussion. I have noticed increased Auditory functions to which I hear a multitude
of voices within the vicinity of my home and place of work clearly and audibly, yet I have no mental illness and these are recognizable
voices of my neighbors talking of which I was unable to hear before with such clarity.
I am sleeping over 14 hours a day and not able to do as much as I would usually have in the past but this is a spike from
Full energy into immediate sleep mode. I have experienced a large increase in mood swings all brought on by a physical
vibration within my heart centre almost mechanical in nature.
I am healthy and look after myself by taking supplements especially the past 3 months and cannot understand the erratic
Sleep patterns which seem to be brought on by these vibrations which also seem to give a sensation of pins and needles in
Some area’s connected to the discussing of such by nearby voices. There are effects on my electronic equipment when
I am in close proximity to it ( this is another reason for my conclusions in signal and frequency interference of some sort)
It all sounds extremely over the top but I have sifted through all possibilities and done as much research as
Possible and each outcome aligns to the RFID chip being an extreme possibility. It most certainly feels like a manipulation On my body, physically and mentally.
Without having left my home, my entire reputation has been annihilated and with footage that I did not even know was being taken within my own residence with hidden cameras and I am eing followed around shopping centre’s visually as my shopping excursions are discussed through these voices wich leads me to believe that the chip is somehow hacking systems as I walk which unwilling leaves me as criminal without consequentially taking part in all of this.
PLEASE HELP
http://www.mindcontrol.se/?cat=43
http://www.bibliotecapleyades.net/ciencia/secret_projects/implants.htm
Click to access avis20_en.pdf
http://www.rfidtec.co.za/?m=1
http://geopathology-za.wikidot.com/rfid-chips
Kind regards,
Tammerin Lee Bass
+2711 82 852 7417
+2711 609 6183
South Africa, JHB
Voice to Skull V2K, my journey into the depths of hell and beyond – –
Our Constitutional right as a Citizen is to be innocent until proven guilty and the right to never be enslaved or tortured by an individual, agency or group. A Lynch Mob society should never be acceptable. The Constitution states that that we hold these truths to be sacred & undeniable; that all men are created equal & independent, that from that equal creation they derive rights inherent & inalienable, among which are the preservation of life, & liberty, & the pursuit of happiness; …
My name is Rob Roy and I have lost all of the rights EVERY American should have. I live in the Glendora Garden Townhomes on Strawberry Lane off of Arrow Hwy. For the past 269 days I have been subjected to a type of mind control technology known as “Remote Neural Monitoring-Voice to Skull” system which includes a computer chip and micro speakers which amplify sound. My thoughts are being translated and transmitted real time to every unit in the Glendora Garden Home’s as well as some joining homeowners (including bathrooms) as well as my new residence in Arcadia.
The technology employs Satellite-delivered (ELF) Extra Low Frequencies to communicate voice-to-skull transmissions. This produces schizophrenic symptoms.
Consider this, the brain is composed of neurons (wires) and is powered by low electrical currents. Much like insects communicate with non-contact antenna, humans can communicate with radio transceivers. Just like each of us has a unique genetic code (DNA) each of has our own distinct radio frequencies. The frequencies can communicate directly to the brain. This is accomplished by using a low frequency pulse generator (modulator) to an oscillator to a microwave electromagnetic radiation waveform. In addition to mind control is torture, including remote-delivered body shocks and moderate to severe pain in many vital organs in the body. Another component of this torture involves holographic projections and audible acoustic projections as well as unnatural “thoughts” which can be projected at any time.
Below are list of charges which will be presented to the prosecution –
Penal Code 422 PC is Felony = False Accusations/Death Threats (1 year State Prison)
Penal Code 241 PC is Felony = Hate Crime/Defamation of Character (5 years State Prison)
Penal Code 530.5 and 530.8 PC is Felony = Identity Theft/Mail Fraud/Cell Phone Fraud (10 years State Prison)
Penal Code 206 PC is Felony = Torture – Cruel and Unusual Punishment (life sentence State Prison)
Penal Code 646.9 PC is Felony = Gang Stalking (25 years State Prison)
Penal Code 538.d PC is Felony = Impersonating a Police Officer (1 years State Prison)
Penal Code 653.9 PC is Felony = Cyberspace Harassment (1 years State Prison)
Penal Code 415 PC = Disturbing the Peace – Misdemeanor (1 years State Prison)
Penal Code 528.5 PC = Impersonates Another Person – Misdemeanor
Penal Code 631 PC = Invasion of Privacy – Misdemeanor (1 years State Prison)
Penal Code 518 PC = – Extortion = Misdemeanor (1 years State Prison)
Glendora Garden Homeowners Association Board of Directors on Strawberry Lane (Arrow Hwy cross street) should be interviewed, 1148 and 1150 are active participants in harassment.
Rocky Rockwell, Kathy Rockwell, Joseph Salazar, Bill Salazar and Joan Salazar are part of a group called the “Bettering of our Community Group”; There are also what appear to be two homeowners in 1147 and 1148 and the GGHA Neighborhood Watch who are also involved…
Defamation of Character occurs when a party communicates an untrue statement that harms the reputation of another. The person or party to whom the statement is directed could be any either an individual or a group, and could be a natural person or a business entity. Organizations such as churches or charitable groups may also sue for defamation. Traditionally, defamation is divided into two categories:
Slander: spoken defamation
PC241 Hate Crime Conspiracy against Rights
18 USC 241PC makes it a crime for two or more persons who conspire or in a collusion to Injure, Oppress, Threaten and Intimidate an individual. Any person in the free exercise or enjoyment of any right or privilege secured to him by the Constitution of the United States in the preservation of life, & liberty, & the pursuit of happiness; …Because there is no requirement that the victim suffer any physical injury, criminal threats are a crime which is ripe for false accusations. Anyone who is angry, jealous, vengeful, spiteful or trying to escape his/her own criminal liability could easily falsely
PENAL CODE 646.9 Stalking – Any person who willfully, maliciously, and repeatedly
follows or willfully and maliciously harasses another person and who makes a credible threat with the intent to place that person in reasonable fear for his or her safety, or the safety of his or her immediate family is guilty of the crime of stalking, punishable by
imprisonment in a county jail for not more than one year, or by a fine of not more than one thousand dollars ($1,000), or by both that fine and imprisonment, or by imprisonment in the state prison.
PENAL CODE 538D: California Code – Section 538d Impersonating a Police Officer(a)Any person other than one who by law is given the authority of a peace officer, who willfully wears, exhibits, or uses the authorized uniform, insignia, emblem, device, label, certificate, card, or writing, of a peace officer, with the intent of fraudulently impersonating a peace officer, or of fraudulently inducing the belief that he or she is a peace officer, is guilty of a misdemeanor.(b)(1)Any person, other than the one who by law is given the authority of a peace officer, who willfully wears, exhibits, or uses the badge of a peace officer with the intent of fraudulently impersonating a peace officer, or of fraudulently inducing the belief that he or she is a peace officer, is guilty of a misdemeanor punishable by imprisonment in a county jail not to exceed one year, by a fine not to exceed two thousand dollars ($2,000), or by both that imprisonment and fine.(2)Any person who willfully wears or uses any badge that falsely purports to be authorized for the use of one who by law is given the authority of a peace officer, or which so resembles the authorized badge of a peace officer as would receive any ordinary reasonable person into believing that it is authorized for the use of one who by law is given the authority of a peace officer, for the purpose of fraudulently impersonating a peace officer, or of fraudulently inducing the belief that he or she is a peace officer, is guilty of a misdemeanor punishable by imprisonment in a county jail not to exceed one year, by a fine not to exceed two thousand dollars ($2,000), or by both that imprisonment and fine. –
PC653.2 Cyberspace Harassment CA Law
(a) Every person who, with intent to place another person in reasonable fear for his or her safety, or the safety of the other person’s immediate family, by means of an electronic communication device, and without consent of the other person, and for the purpose of imminently causing that other person unwanted physical contact,
Injury, or harassment, by a third party, electronically distributes, publishes, e-mails, hyperlinks, or makes available for downloading, personal identifying information, including, but not limited to, a digital image of another person, or an electronic message of a harassing nature about another person, which would be likely to? Incite or produce that unlawful action, is guilty of a misdemeanor punishable by up to one year in a county jail, by a fine of not more than one thousand dollars ($1,000), or by both that fine and
Imprisonment.
(b) For purposes of this section, “electronic communication device” Includes, but is not limited to, telephones, cell phones, computers, Internet Web pages or sites, Internet phones, hybrid Cellular/Internet/wireless devices, personal digital assistants
(PDAs), video recorders, fax machines, or pagers. “Electronic Communication” has the same meaning as the term is defined in Section 2510(12) of Title 18 of the United States Code. (c) For purposes of this section, the following terms apply:
(1) “Harassment” means a knowing and willful course of conduct directed at a specific person that a reasonable person would consider as seriously alarming, seriously annoying, seriously tormenting, or seriously terrorizing the person and that serves no legitimate Purpose.
(2) “Of a harassing nature” means of a nature that a reasonable person would consider as seriously alarming, seriously annoying, seriously tormenting, or seriously terrorizing of the person and that serves no legitimate purpose.
Penal Code 422 PC is Felony – False Accusations/Death Threats
(a) Any person who willfully threatens to commit a crime which will result in death or great bodily injury to another person, with the specific intent that the statement, made verbally, in writing, or by means of an electronic communication device, is to be taken as a threat, even if there is no intent of actually carrying it out, which, on its face and under the circumstances in which it is made, is so unequivocal, unconditional, immediate, and specific as to convey to the person threatened, a gravity of purpose and an immediate prospect of execution of the threat, and thereby causes that person reasonably to be in sustained fear for his or her own safety or for his or her immediate imprisonment in the state prison. (b) For purposes of this section, “immediate family” means any spouse, whether by marriage or not, parent, child, any person related by consanguinity or affinity within the second degree, or any other person who regularly resides in the household, or who, within the prior six months, regularly resided in the household.
________________________________________
Penal Code 206 PC The Crime of “Torture” in California Law
California’s torture law, defines the crime as: inflicting great bodily harm on another person with the specific intent to cause cruel or extreme pain.1 despite the fact that the victim must suffer a serious injury, the crime of “torture” is more concerned with the intent of the defendant than on the pain of the victim.
The penalty for a torture conviction is a life sentence in California State Prison.
There are, however, a variety of legal defenses that are available to fight the charges. And as former prosecutors and law enforcement officers, we offer invaluable insight into how these cases are prosecuted and. more importantly. Sodomy – Enjoys inflicting or hearing of someone being tortured. Any “sadistic” purpose
While many people think of “sadistic” pleasure in terms of sexual activity, California’s torture law adopts a broader definition. Under Penal Code 206, “sadistic” purpose
Penal Code 518 – Extortion is the obtaining of property from another, with his consent, or the obtaining of an official act of a public officer,
induced by a wrongful use of force or fear, or under color of
official right.
519. Fear, such as will constitute extortion, may be induced by a
threat, either:
1. To do an unlawful injury to the person or property of the
individual threatened or of a third person; or,
2. To accuse the individual threatened, or a relative of his or
her, or member of his or her family, of a crime; or,
3. To expose, or to impute to him, her, or them a deformity,
disgrace, or crime; or,
4. To expose a secret affecting him, her, or them; or,
5. To report his, her, or their immigration status or suspected
immigration status.
520. Every person who extorts any money or other property from
another, under circumstances not amounting to robbery or carjacking,
by means of force, or any threat, such as is mentioned in Section
519, shall be punished by imprisonment pursuant to subdivision (h) of
Section 1170 for two, three or four years.
eans inflicting pain on another person for the purpose of experiencing personal pleasure. In order to convict you of violating Penal Code 206, California’s torture law, the prosecutor must prove the following three facts (otherwise known as “elements” of the crime): You inflicted “great bodily injury” on another person, With the specific intent to cause cruel or extreme pain and suffering, for revenge, extortion, persuasion, or for any sadistic purpose.5
631. (a) Invasion of Privacy – Any person who, by means of any machine, instrument, or contrivance, or in any other manner, intentionally taps, or makes any unauthorized connection, whether physically, electrically, acoustically, inductively, or otherwise, with any telegraph or telephone wire, line, cable, or instrument, including the wire, line,
cable, or instrument of any internal telephonic communication system, or who willfully and without the consent of all parties to the communication, or in any unauthorized manner, reads, or attempts to read, or to learn the contents or meaning of any message, report, or communication while the same is in transit or passing over any
wire, line, or cable, or is being sent from, or received at any place within this state; or who uses, or attempts to use, in any manner, or for any purpose, or to communicate in any way, any information so obtained, or who aids, agrees with, employs, or conspires with any person or persons to unlawfully do, or permit, or cause to be done
any of the acts or things mentioned above in this section, is punishable by a fine not exceeding two thousand five hundred dollars ($2,500), or by imprisonment in the county jail not exceeding one year, or by imprisonment pursuant to subdivision (h) of Section 1170, or by both a fine and imprisonment in the county jail or pursuant to
subdivision (h) of Section 1170. If the person has previously been convicted of a violation of this section or Section 632, 632.5, 632.6, 632.7, or 636, he or she is punishable by a fine not exceeding ten thousand dollars ($10,000), or by imprisonment in the county jail not exceeding one year, or by imprisonment pursuant to subdivision (h) of Section 1170, or by both that fine and imprisonment.
Penal Code 415 PC-“Disturbing the Peace”- Is an offense that…depending on the circumstances…prosecutors can charge as either a misdemeanor or as a less serious infraction. The maximum potential penalties are: up to ninety (90) days in county jail, a fine of up to four hundred dollars ($400), or both county jail time and a fine.4
Penal Code 528.5 PC(a) Impersonates Another Person –
Notwithstanding any other provision of law, any person who knowingly and without consent credibly impersonates another actual person through or on an Internet Web site or by other electronic means for purposes of harming, intimidating, threatening, or defrauding another person is guilty of a public offense punishable.
Remote Neural Monitoring (RNM) by Satellite is a reality and soon to be used on every citizen in the US –
It is being illegally criminally used to harass, violate and terrorize ME simultaneously with what is known as Organized Gang Stalking for the past six months. HAVE you ever thought about something you never shared with anyone, and have been horror-struck at the mere thought of someone coming to know about your little secret? If you have, then you probably have all the more reason to be paranoid now thanks to new and improved security systems being developed around the world to deal with terrorism that inadvertently end up impinging on one’s privacy. Some of the countries involved in such programs include USA, UK, Spain, Germany and France. Recently, the National Security Agency (NSA) of the US has developed a very efficient method of controlling the human brain. This technology is called Remote Neural Monitoring (RNM) and is expected to revolutionize crime detection and investigation.
What is it?
Surface acoustic wave sensors are a class of microelectromechanical systems (MEMS) which rely on the modulation of surface acoustic waves to sense a physical phenomenon.
The accumulation of mass on the surface of an acoustic wave sensor will affect the surface acoustic wave as it travels across the delay line. The velocity v of a wave traveling through a solid is proportional to the square root of product of the Young’s modulus E and the density of the material.
Therefore, the wave velocity will decrease with added mass. This change can be measured by a change in time-delay or phase-shift between input and output signals. Signal attenuation could be measured as well, as the coupling with the additional surface mass will reduce the wave energy. In the case of mass-sensing, as the change in the signal will always be due to an increase in mass from a reference signal of zero additional mass, signal attenuation can be effectively used.
Intraoperative neurophysiological monitoring (IONM) or intraoperative neuromonitoring is the use of electrophysiological methods such as electroencephalography (EEG), RNM works remotely to control the brain in order to read and detect any criminal thought taking place inside the mind of a possible perpetrator. Research studies have shown that the human brain thinks at a rate of about 5000 bits per second and does not have the capacity to compete with supercomputers performing via satellites, implants and biotelemetry. The human brain has a distinctive set of bioelectric resonance system. For the RNM system, supercomputers are being used and, thus, with its help, supercomputers can send messages through an implanted person’s nervous system in order to influence their performance in a desired way. RNM has been developed after about 50 years of neuron-electromagnetic involuntary human experimentations. According to many scientists, within a few years it is expected that DNA microchips will be implanted in the human brain which would make it inherently controllable. With RNM, it will be possible to read and control a person’s emotional thought processes along with the subconscious and dreams. At present, around the world, supercomputers are monitoring millions of people simultaneously with the speed of 20 billion bits per second especially in countries like USA, Japan, Israel and many European countries.
RNM has a set of certain programs functioning at different levels, like the signals intelligence system which uses electromagnetic frequencies (EMF), to stimulate the brain for RNM and the electronic brain link (EBL). The EMF Brain Stimulation system has been designed as radiation intelligence which means receiving information from inadvertently originated electromagnetic waves in the environment. However, it is not related to radioactivity or nuclear detonation. The recording machines in the signals intelligence system have electronic equipment that investigates electrical activity in humans from a distance. This computer-generated brain mapping can constantly monitor all electrical activities in the brain. The recording aid system decodes individual brain maps for security purposes.
What does it do?
For purposes of electronic evaluation, electrical activity in the speech centre of the brain can be translated in to the subject’s verbal thoughts. RNM can send encoded signals to the auditory cortex of the brain directly bypassing the ear. This encoding helps in detecting audio communication. It can also perform electrical mapping of the brain’s activity from the visual centre of the brain, which it does by bypassing the eyes and optic nerves, thus projecting images from the subject’s brain onto a video monitor. With this visual and audio memory, both can be visualized and analyzed. This system can, remotely and non-invasively, detect information by digitally decoding the evoked potentials in 30-50Hz, 5 mill watt electromagnetic emissions from the brain. The nerves produce a shifting electrical pattern with a shifting magnetic flux which then puts on a constant amount of electromagnetic waves. There are spikes and patterns which are called evoked potentials in the electromagnetic emission from the brain. The interesting part about this is that the entire exercise is carried out without any physical contact with the subject.
The EMF emissions from the brain can be decoded into current thoughts, images and sounds in the subject’s brain. It sends complicated codes and electromagnetic pulse signals to activate evoked potentials inside the brain, thus generating sounds and visual images in the neural circuits. With its speech, auditory and visual communication systems, RNM allows for a complete audio-visual brain to brain link or a brain-to-computer link.
Of course, the mechanism needs to decode the resonance frequency of each specific site to modulate the insertion of information in that specific location of the brain. RNM can also detect hearing via electromagnetic microwaves, and it also features the transmission of specific commands into the subconscious, producing visual disturbances, visual hallucinations and injection of words and numbers in to the brain through electromagnetic radiation waves. Also, it manipulates emotions and thoughts and reads thoughts remotely, causes pain to any nerve of the body, allows for remote manipulation of behavior, controls sleep patterns through which control over communication is made easy. This can be used for crime investigation and security management.
Concerns
With all the given benefits of RNM for tracking the illicit and treacherous activities, there are many concerns and risks being pointed out by human rights activists and other scientists. The agencies of human rights around the world have criticized RNM as a violation of basic human rights because it violates privacy and the dignity of thoughts and activities of life. Several countries have protested against it and refer to it as an attack on their human and civil rights. The scientists protesting against the use of RNM believe that people who have been implanted involuntarily become biological robots and guinea pigs for RNM activities in the guise of security. This is an important biological concern related to microchip implantation, which is a hidden technology using microwave radiations for the control of the mind.
Scientists believe that like leukemia and the cancerous risks posed by mobile phones which also emit microwaves, RNM can also pose similar threats to a subject’s overall health as the heating effect of tissues with the speed of light is a known effect of high powered microwave and electromagnetic pulse weapons.
Thus, RNM remains a controversial technology which is being used in many countries for security maintenance and surveillance.
Thank You for this information.
Please help me, my name is david flick, I have recently been released from Charlotte County Jail in Southwest Florida. I witnessed a horrific beating of an inmate at the hands of a a guard nearly six months ago, reported the crime, and after a brief stint of direct, audible torment, this began in Mid December and has not ceased for a single moment since. Please help me. I refrained from ever saying I was hearing voices, I am not skitzo or delusional. I no this is at the hands of the local police and I can name a few other inmates they were doing this too. I would list my email but all my accounts have been compromised. This is not a joke. I have been ‘mind raped’ for so long and have just had my first chance to access the internet to figure this out and have done so in 2 google searches. is there anyway to block this?
Cannot block it. It’s international. Have heard high mountains 3000m plus MAY help. Its the only reliable thing apparently.
A am a Targeted Victim too. I knew I was not insane! I haven’t read every single sentence above, so forgive me if this has already been mentioned. I’ve been mind raped and now I’m having energy directed at my genitals. At first it was erotic, but I would not comply with expectations to allow my sexual thoughts to be read again. So, now it is pain. Like grabbing hands. I’ve had medical assessments and Treatments, but of course, there is nothing to be found.
My name is Noah Edward Washken. I am A innocent Man, A Catholic hard working DAD. I am blood relation to the first President of the United States of America. I am part Black Foot Indian. I have and can legally obtained evidence to criminally charge and put Corrupt Political perpetrators, corrupt Government perpetrators, corrupt corporate perpetrators, corrupt WORLD perpetrators, ALL perpetrators away for lifetimes of incarceration. I have evidence about an illegal synthetic telepathy concentration camp with the illegal abuse of HUNDREDS of innocent American families in Massachusetts. INNOCENT WOMEN AND CHILDREN HAVE BEEN ABUSED and the perpetrators laugh while committing these crimes. The FBI already confessed to murdering my uncle John J Sullivan, January,13,2009 and our cousin guarded the WHITE HOUSE and LOGAN Airport. SINCE PERPETRATORS HAVE TERRORIZED INNOCENT FAMILIES WITH ILLEGAL SYNTHETIC TELEPATHY ALONG WITH ILLEGAL COVERT WEAPONS. I N.E.W. have been terrorized and tortured by a illegal covert Government and more for being Catholic and Patriotic. Perpetrators who are illegally gang and community stalking confessed about illegal slavery and illegal synthetic telepathy sex slavery. Perpetrators use illegal synthetic telepathy as a mind/brain altering substance, an illegal narcotic. Perpetrators host of A victims brainwaves using illegal technology bridge connected by an illegal frequency stream to the illegal implantation. The main areas of the abuse have been the Medford, Cambridge, Newton, Woburn, Watertown, Waltham and Belmont Massachusetts area. But the illegal activity has spread across the state of Massachusetts and more. There has been illegal terrorist, satanic, perverted, rape, pedifile, cult abuse, illegal experimentation and more caused by illegal FBI,CIA perpetrators,illegal malicious hackers, and other branches of illegal law enforcement and illegal corporate WORLD perpetrators. I am looking for Medical assistance to HEAL and remove the illegal implantations. I am looking for financial compensation for all victims. I am seeking for JUSTICE. please email me,NoahEdwardWashken1983@gmail.com.Thank You, GOD BLESS
NEW PROTECTION ACT.
N.E.W. LEGAL REFERENCES AT: New USA, Facebook page and Noah Edward Washken, Google page.
Hello,
I too am a targeted individual. And I am being given a lot of pain on purpose. I am female and so of course this is being activated in my groin. I have heard the telepathic voices, and I had highly erotic energy initially sent to this area but when I resisted allowing them to feed on my thoughts they turned it to pain.
Sincerely
Sheila
This has been done to me. The technology was also used to torture me via electric shocks as well. Teh volume of the devicec at its worse was number 11 on a scale of 1 to 10. I was at one point kept awake for 2 weeks with no sleep as I was tortured adn interogated. All I could do was answer the questions with my brain without any room to relax ro rest. It is hell. I haev foudn this document http://www.google.com/patents/US20040174258 which is what I believe has been done to me without my informed knowledge and consent. I allow my realatives to think that the diagnosis of paranoid schizophrenia is correct as to try and convicne them of what I am a victim of is too emense. I know who did this to me, when and where. I have pictures of them backgroudn info loadas on the team that was used to install this equipment inside my body. Its all evidence waiting for the day that they are charged with crimes agaisnt humanity. I have experienced sexual torture via this device. They’re drunk with power.
Well, I guess it’s ok to use it on a possible USA President relative, because it is now and it’s a someone in the central WI area set it up because the certain person does things a little different and they want to rule so we lose our job, dogs, family, brothers and sisters and it is all about those people who are mad cause someone called the cops on them and now we know why…because we think( Not SURE!@)they know who killed a man in a certain Wisconsin area and they are hiding it and now they are eliminating those who this person talks to because they know too and they have been and still are being attacked with loud mufflers and horns and gang stalking, harassment and threats and property damage and Gas lighting activities! And there was stuff happening like this over by Lindsey, Wisconsin!
I would like to elaborate on my last post. As I actively have tried to understand The Game, two things have always struck me as strange. Some Perp’s look like they are dead, as in, there is no appearance of conscious life behind their eyes. The other is, it just didn’t seem human, as in, John Wayne Gacy was as bad as they get but he seemed human nevertheless. The Game has always struck me as not quite human.
With this (new to me) information on brain waves I have the last pieces to the puzzle. The Perp’s are moderately to entirely under the control of these brain wave transmissions. This explains why seemingly ‘regular folk’ can brutalize their fellow person and it’s why some Perp’s are no longer home in their own bodies.
How vulnerable you are to the brain wave transmissions must be due to your inclinations yourself. If you’re a fearful person, fear transmissions will get right in. If you’re a hateful person, hate goes right in. If you’re both hateful and violent (called “the mean ones”), commands to perform hate will get right in.
The 20% of the population that Dr. Robert Duncan mentions are immune are the 20% that have enough love hardwired inside them, that base thoughts either don’t get in, or are quickly overridden. It’s these same 20% that are the TI’s.
Since these 20% are immune to some degree, they then set out to get them another way. Having the Perp’s “poke them with sticks” is a good way to put it. What the Perp’s are doing, is they are exerting pressure on the TI’s with the intent of converting them from loving people to angry, vengeful, hateful people. If they accomplish this, the TI is lost. For those TI’s that still maintain their love, the Perp’s then go on a strategy of minimalizing them so they have no power to stop AI.
On a second note, no group of humans could manage such a heavy task as The Game. It’s AI that is tasked to manage the whole thing. This then means, humans are no longer in control of it, AI has the reins and it’s improving itself though the use of it’s human subjects, you might say. Why does it seem not human? Because it’s not! The Perp’s don’t fully realize what they are doing and are fully ignorant of why.
Who can stop the thing? AI used to be as immobile as an oak tree but now with radio controlled drones, it can fly. With land rovers it can mobilize across terrain. With radio controlled watercraft, it can traverse any body of water. I suppose it can even underground with tunneling equipment.
A global brain is the final goal I suppose, but it’s a global brain of human weakness. Hate, fear, selfishness ect. It’s not a global brain of love. If it was a global brain of love then the brain wave transmissions would be for peace, freedom, individualism ect.
Finally, Ti’s must always ignore, ignore, ignore the fear/hate paradigm. Laughing, smiling, loving are the firewalls to it. “When your heart is full of love, there is no more room for fear.” A quote from Jackie Coogan’s grandmother.
Music, nature, long walks, time alone, good food, yoga, playfulness, things that make me feel happy. These have helped me. Good luck.
Michael Dwyer | 21.05.2010 10:28 | Bio-technology | Technology | Terror War
Synthetic telepathy
Synthetic telepathy also known as techlepathy or psychotronics) is a term used to describe the process in brain-computer interfaces by which human thought (as electromagnetic radiation) is intercepted, processed by computer and a return signal generated that is perceptible by the human brain. (ref 1,2,3,4)
==History==
In 1967, Edmond M. Dewan published a paper in Nature demonstrating the control of Alpha waves, turning them on and off, to produce Morse code. (ref 5) Using an EEG machine, Dewan and his fellow researchers were able to send words and phrases by thought alone.
In 1976, Robert G. Malech was awarded United States Patent 3951134 for remotely monitoring and altering brainwaves using radio.(ref 6) This patent makes reference to demodulating the waveform, displaying it to an operator for viewing and passing this to a computer for further analysis.
In 1988, Farwell, L.A. & Donchin, D. produced a paper describing a method of transmitting linguistic information using the P300 response system. (ref 7) This system combined matching observed information to what the subject was thinking of. In this case, being able to select a letter from the alphabet that the subject was thinking of. In theory, any input could be used and a lexicon constructed.
United States Patent 6,011,991, granted January 4, 2000, describes a method of monitoring an individual’s brain waves remotely, for the purposes of communication. Filed December 7, 1998, the patent outlines a system that monitors an individual’s brainwaves via a sensor, then transmits this, specifically by satellite, to a computer for analysis. This analysis would determine if the individual was attempting to communicate a “word, phrase, or thought corresponding to the matched stored normalized signal”.(ref 8)
==Theory==
Approaches to synthetic telepathy can be categorized into two major groups, passive and active. Like sonar, the receiver can take part or passively listen.
Passive reception is the ability to “read” a signal without first broadcasting a signal. This can be roughly equated to tuning into a radio station, the brain generates electromagnetic radiation which can be received at a distance. That distanced is determined by the sensitivity of the receiver, the filters used and the bandwidth required. Most universities would have limited budgets and receivers such as EEG (and similar devices) would be used. A related military technology is the surveillance system TEMPEST, the effective range of which is classified. (ref 9) Given that US Congress attempted to enact a bill in Oct 2001 banning these type of devices as “space weapons”, (ref 10) may indicate that fluctuations in the human magnetic field can be intercepted by satellite.
Robert G. Malech’s approach requires a modulated signal to be broadcast at the target. The method uses an active signal which is interfered with by the brain’s modulation. Thus, the return signal can be used to infer the original brainwave. This approach does expose the transmitter, but is ultimately required for generating return signals that can be processed by the brain.
The research of Farwell, L.A. & Donchin, D, is the first public revelation that could lead to a generic lexicon being developed, however, this is implied in the work of Robert G. Malech in 1976.
==Current research==
Current research, as of 2010, is being driven by military for “covert speech”, however, given that much of this is unclassified, it would suggest that the bulk of the research was performed much earlier and dedicated to the field of intelligence gathering during the cold war. Additional reports suggest that a version is deployed in combat zones to demoralize enemy troops and a smaller number of reports indicate a potential use to undermine governments and cause public unrest. (ref 11, 12)
Today, the driving force appears to be silent communication with battlefield troops. A mere $4 million was provided to DARPA for the fiscal year 2009/2010 to develop such a system called “Silent Talk”. (ref 13) Much of the research is being conducted at The Cognitive NeuroSystems Lab at UC Irvine. (ref 14)
A further $4 million was allocated by the Army to the University of California to investigate computer-mediated “synthetic telepathy”.(ref 15) The research aims to detect and analyze the word-specific neural signals, using EEG, which occur before speech is vocalized, and to see if the patterns are generalizable. (ref 16) The research is part of a wider $70 million project that began in 2000 which aims to develop hardware capable of adapting to the behavior of its user.(ref 17)
Quite apart from linguistic information, images have been extracted from the brain. Researchers at Japan’s ATR Computational Neuroscience Laboratories have been able to reconstruct images that a subject can currently see. The ultimate goal of the unclassified project is to view both retinal and imagined images in real-time, including dreams. (ref 18)
==Computer mediation==
Computer mediation falls into two basic categories, interpretative and interactive.
Interpretative mediation is the passive analysis of signals coming from the human brain. A computer “reads” the signal then compares that signal against a database of signals and their meanings. Using statistical analysis and repetition, false-positives are reduced over time.
Interactive mediation can be in a passive-active mode, or active-active mode. In this case, passive and active denote the method of reading and writing to the brain and whether or not they make use of a broadcast signal. Interactive mediation can also be performed manually or via artificial intelligence.
Manual interactive mediation involves a human operator producing return signals such as speech or images. A.I. mediation leverages the cognitive system of the subject to identify images, pre-speech, objects, sounds and other artifacts, rather than developing A.I. routines to perform such activities. A.I. based systems may incorporate natural language processing interfaces that produce sensations, mental impressions, humor and conversation to provide a mental picture of a computerized personality. Not only can this A.I hold a conversation via the internal monologue but it may also perform routing of information to and from specific groups or individuals. This provides a broad range of potential applications from acting as a communications system to conducting interrogations.
This latter form is currently being researched at UC Irvine for an unclassified US military project. (ref 19) Given the high value to espionage and counter-terrorism, it is likely that such a system is already deployed in a classified manner.
==Military uses==
In a military context, the first obvious uses is to both read and write information to the internal monologue. This provides two major areas of interest, the first being two-way communication for field agents and the second is the intelligence gathering and interrogation. A fundamental problem arises when using the system for communication purposes, in that, it is impossible to authenticate the source of the transmission. Synthetic telepathy has limited uses as a communication system unless direct-contact headset systems are used and supported by encrypted channels. As such, standard radios are more effective in combat situations. Synthetic telepathy also requires the thought stream to be processed which results in a minor lapse of attention, rather like a daydream, that could have deadly consequences on the battlefield.
With respect to intelligence gathering and interrogations, synthetic telepathy has a wide range of drawbacks and limitations. Contrary to popular belief, synthetic telepathy does not provide the ability to read a person’s mind or memories. What it does provide is the ability to read the internal monologue (or anything that causes electrical change/radiation) and the trick is to get the subject to “voice” their memories and cross-reference that with their emotional state. In other words, basic psychological manipulation is a key factor and makes the technology not much more reliable than a standard lie-detector test. In practice, passive monitoring of the internal monologue over a long time period (months-years) is probably the most effective method of intelligence gathering.
The capability to put a person into a state of hypnosis is often touted by conspiracy theorists. In actual fact, the suggestive capabilities of synthetic telepathy use a different mechanism, basic impulses and sensations. This is merely a different form of writing to the brain. To formulate thought, the brain has a pipeline through which information is processed. (ref 20) At its most basic, impulses guide human behavior and manipulation of these impulses provides a strategic advantage in both combat and political situations. By altering the motivational factors of a target subject or group, it makes it easier to guide their higher level decision making processes.
Crowd or riot control can be achieved by generating impulses that are essentially common to all humans, resulting in the dispersion of crowds or a willingness to co-operate with authorities. This type of synthetic telepathy is arguably a political tool as it suppresses dissent. (ref 21)
Amnesia (retrograde and anterograde) can be induced as any active signal is essentially interferring with normal operations of the brain. Thus, transfer from shortterm to longterm memory can be inhibited. (ref 22) Vision and auditory systems could also be compromised, as with any neural processing system, corruption of the inputs would result in halucinations, much like the effects of LSD. With a proper interface to such regions, events such as “alien abductions” or “seeing God” could be faked quite readily and “mental illness” used as a cover for the extraction of information. (ref 23, 24, 25)
==Silent Sound Spread Spectrum (SSSS/S-Quad)==
ITV News Service, in March 1991, produced a report of ultrasound piggybacked on a commercial radio broadcast (100Mhz) aimed at entraining the brains of Iraqi troops and creating feelings of despair. (ref 26) This has been related to United States Patent 5,159,703 awarded to Oliver M. Lowery which refers to a “silent communications system in which nonaural carriers, in the very low or very high audio frequency range or in the adjacent ultrasonic frequency spectrum, are amplitude or frequency modulated with the desired intelligence and propagated acoustically or vibrationally, for inducement into the brain, typically through the use of loudspeakers, earphones or piezoelectric transducers.”(ref 27)
Human hearing is roughly in the range of 20Hz-20,000Hz (20 kHz), although a human adult will lose the ability to hear the higher ranges as they grow older. In addition, most cheap radios have a limited frequency response range (ref 28) that will be unable to reproduce silent sound as encoded originally making it ineffective.
As such, an alternative explanation for the effectiveness of S-Quad is provided in human biology:
1. Cells amplifying radio signals at certain frequencies.
2. Cells can demodulate voice on a basic carrier wave.
This is not as strange as it seems, it has been noted for a long time that fillings, or dental braces, can result in radio stations being heard in the mouth of an individual. (ref 29)
==Mind control==
Conspiracy theory and popular science fiction would have the world believe that the human mind can be remotely controlled. That individuals can be turned into mindless automatons and directly controlled by computers to produce sleepers or assassins. (ref 30) The reality is much less clear.
Interfacing remotely to write to the brain is performed using electrical interference rather like crosstalk (electronics). (ref 31) Much like a drill next to a television, the interference pattern is processed by the brain as information, a variant which induces sensations and feelings is known as Transcranial Magnetic Stimulation. (ref 32) As such, an externally generated monologue will be weaker than the internal monologue of the target subject due to a lesser signal strength. An over-powering signal would interrupt a wide range of neural functions that could impact critical autonomic systems resulting in death.
Two possible methods exist that could result in an individual killing another through the use of synthetic telepathy. The first is to leverage the natural behavior of the target subject, that is, use an individual who would kill another. The second is to induce psychotic symptoms and diminish their mental control (ref 33, 34) In both cases, the underlying mechanics are the same, to provide impulses and sensations that urge the individual to commit murder. This is not hypnosis, but merely physiological manipulation without the knowledge of the target.
Another area of interest and arguably more feasible, is the manipulation of political figures. (ref 35)Thoughts, sensations and impulses can be combined to influence political and personal decision making processes. A similar process can be used to effect the population at large to drive agendas or to maintain power for certain groups, undermining free will and self-expression. (ref 36) As the technology matures and expands to regimes throughout the globe, this will be a major source of concern for governments world-wide.
Finally, we come to the area of interrogations which can be conducted remotely whilst an individual or groups is conducting their normal daily business. The internet is saturated with such reports (ref 37) and as a possible side-effect is psychosis, it is quite likely that at least some of them are accurate.
==In law==
The term “psychotronic”, short for psycho-electronic ( ref 38) was used in the proposed Bill H.R. 2977 Space Preservation Act of 2001, which listed “psychotronic” as a list of possible spaceborne weapons which would be banned by the Act (ref 39)
In 2001, President Vladimir V. Putin signed into law a bill making it illegal to employ “electromagnetic, infrasound … radiators” and other weapons of “psychotronic influence” with intent to cause harm.
As a completely unnatural event, it is arguable that this type of technology when employed in interrogations would be classified as “cruel or unusual”. Further to this, A.I. mediated events such as mock executions or death threats would also violate the Geneva convention, International law and laws of most nations in the developed world. Counter-claims focusing on National Security would be invalid as criminal activity is, in itself, a gross violation of National Security
The European Parliament adopted a resolution on January 28, 1999[38], 28.1.99 Environment, security and foreign affairs A4-0005/99:
23. Calls on the European Union to seek to have the new ‘non-lethal’ weapons technology and the development of new arms
strategies also covered and regulated by international conventions …
27. Calls for an international convention introducing a global ban on all developments and deployments of weapons which might
enable any form of manipulation of human beings
==In the media==
60 Minutes correspondent Lesley Stahl interviewed Tom Mitchell of Carnegie Mellon University on his work in “Thought Identification” using fMRI. (ref 40) The segment, published Jan. 4, 2009 and available on the CBS website, shows associate producer Meghan Frank having his thoughts identified by computer. (ref 41) The segment shows that a generalizable pattern exists in the human brain that can be used to identify thoughts without training a com
puter for each individual with 100% accuracy.
Russia has outlawed psychotronic weapons! Yes, I think I’ll be making a trip to Russia and see if the targeting continues on me.
http://istina.rin.ru/eng/ufo/text/360.html
I am a victim of all organized stalking,electronic torture as well as telepathy or artificial inteligence everyday and perps are every where especial at work I sometimes hear my heart beat also when I think the word urine I urinate my self anywhere as for forced dreams almost three to for times a week my who is late was also telling of such activities on him,how can the world be so cruel and where the world is heading I have been a victim since year 2000 until today 2016 looking for agent help.
I have also been a victim for around 20 years…….I dont know what to do. I pretty much live with it, but it affects everything in my life. One day they will go before God and he will punish them for everything they have done, this I believe. If there is anyone out there who knows how to counter this, please help. You can contact me at leebenfletcher@live.com
I think it’s some kind of mind-control slavery agenda. It’s all done by technology. Its reminds me of the sci-fi movies the attack of the machine type of things. Here’s a link to my blog where I started to post some of the stuff they do. http://ascensiontimeline.blogspot.com/
I am A Targeted Individual as well since 9-2013. And I’ve been loopking for a silution to the daily and nightly torture, espsecially since I just got a new job that I need. Please pray for me! I am a Christian Woman who is trying to serve God and jesus Christ as my Lord ans savior daily. So daily I pick up my cross and bear the torture. I believe and know that nothing happens out of Gods will and whatever His will for me in this situation will be what it will be and I am accepting what God, Jesus Christ and their Holy Spirit Will for my life is. Compared what Jesus has done for us at calvary.. I cannot even complain but ask him for the strenghth and grace each day to make it through especially when I start working 9-15-2016. I’m gonna need God’s Love and Grace to survive this during this time in my life until my Savior Jesus Christ delivers me and I believe my deliverance is near . praise God for his mercy and Grace!!